
As someone who has been working with telco Kubernetes for a while, I know firsthand how challenging it can be to ensure that our infrastructure is reliable and performs well. With all the complex components and telco-specific requirements, testing can often feel like a daunting task. In this blog post, we’ll explore the features and benefits of Infractl and how it can transform the way you test and debug your Kubernetes clusters.
Table of contents
Open Table of contents
Understanding the Need for Infractl
Now, I know what you might be thinking: “Another testing tool? What makes Infractl so special?”
Infractl is designed with telco Kubernetes in mind. It understands the unique challenges we face and provides a simple and efficient way to test our infrastructure. Whether you need to spin up pods, check Multus interfaces, validate net-attach-def configurations, or verify sysctl parameters, Infractl has got you covered.
One of the things I love about Infractl is how it automates the testing process. Instead of spending hours manually setting up and running tests, Infractl does the heavy lifting for you. It saves you time and effort, allowing you to focus on what matters most – building awesome telco applications. ⏰
Key Features of Infractl
Multus and Whereabouts Testing
Infractl simplifies the testing of Multus, a vital CNI plugin that enables the attachment of multiple network interfaces to pods in telco environments. With Infractl, you can effortlessly create test pods, verify the creation of net-attach-def resources, and ensure that pods are correctly assigned with multiple network interfaces to support telco workloads.It also checks and validates the Whereabouts IPAM cni. Here’s a code snippet that demonstrates how Infractl creates a test pod with Multus in a telco Kubernetes setup:
testPod := &corev1.Pod{
ObjectMeta: metav1.ObjectMeta{
Name: podConfig.Name,
Namespace: namespace,
Annotations: map[string]string{
"k8s.v1.cni.cncf.io/networks": podConfig.NetAttachDefName,
},
},
Spec: corev1.PodSpec{
Containers: []corev1.Container{
{
Name: "test-container",
Image: "nicolaka/netshoot",
Command: []string{"sleep", "infinity"},
},
},
},
}
Usage:
infractl multus -f variable.yaml --kubeconfig config
Example output:
Terminal User Interface(TUI)
The infractl multus --ui opens a beautiful terminal user interface(TUI) where you can manually enter your multus and whereabouts information if you do not want to use the variable.yaml file.
variable.yaml file:
❯ cat variable.yaml
netAttachDefs:
- name: ipvlan-net-attach-def-host-local
config:
cniVersion: "0.3.0"
type: "ipvlan"
master: "eth0"
ipam:
type: "host-local"
subnet: "100.71.144.0/24"
rangeStart: "100.71.144.221"
rangeEnd: "100.71.144.221"
gateway: "100.71.144.1"
- name: ipvlan-net-attach-def-wherabouts
config:
cniVersion: "0.3.0"
type: "ipvlan"
master: "eth0"
ipam:
type: "whereabouts"
range: "100.71.144.0/24"
range_start: "100.71.144.222"
range_end: "100.71.144.223"
gateway: "100.71.144.1"
pods:
- name: ipvlan-pod
netAttachDefName: ipvlan-net-attach-def-host-local
- name: ipvlan-pod-2
netAttachDefName: ipvlan-net-attach-def-wherabouts
- name: ipvlan-pod-3
netAttachDefName: ipvlan-net-attach-def-wherabouts
SSH into Nodes
Infractl offers a seamless way to SSH into Kubernetes nodes directly from your CLI. With the infractl ssh command, you can easily access a node’s shell, even when it doesn’t have an SSH server running or when you don’t have the required credentials. This feature proves invaluable for troubleshooting and performing ad-hoc tasks on telco Kubernetes nodes. Here’s an example of how to SSH into a Kubernetes node using Infractl
infractl ssh my-cluster-md-0-9kwml-76b6b8d476xnzbds-mvzlf
Example Output:
Resource Utilization Monitoring
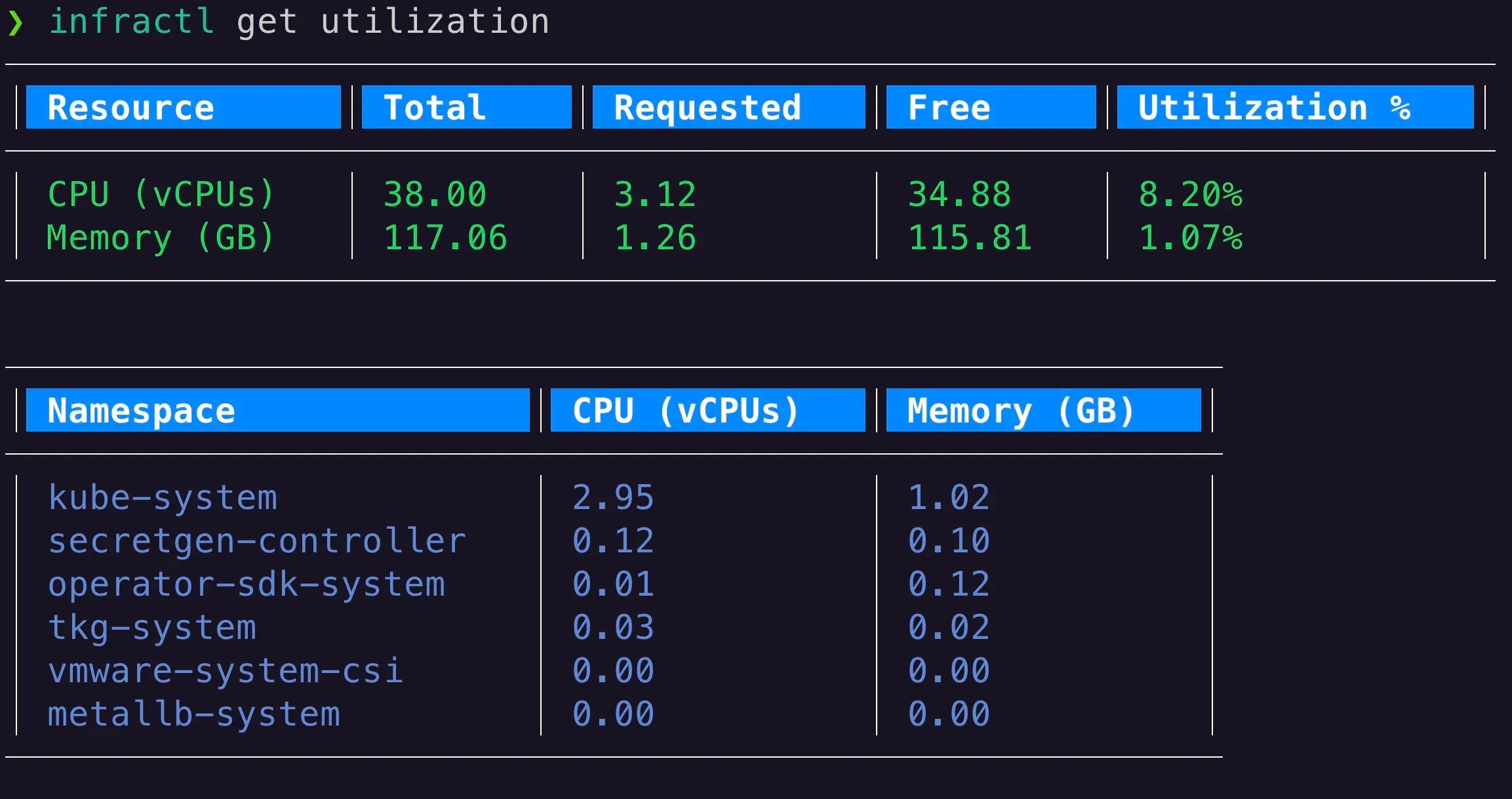
Infractl offers a powerful feature to monitor resource utilization across your Kubernetes cluster. With the infractl get utilization command, you can quickly retrieve information about CPU and memory usage at both the cluster and namespace levels. This functionality helps you identify resource bottlenecks and optimize your cluster’s performance. Here’s a code snippet that showcases how Infractl retrieves resource utilization data
infractl get utilization
Example Output:
Sysctl Testing for Telco Requirements
Infractl enables you to easily test sysctl parameters on your Kubernetes nodes. With the infractl sysctl command, you can verify that the required sysctl settings are correctly configured, ensuring the optimal performance and security of your cluster.
Example Output:
✓ Sysctl parameter net.ipv4.ip_forward is set to 1
✓ Sysctl parameter net.ipv4.conf.all.rp_filter is set to 0
Quick Namespace and Context Switching
Infractl enhances the efficiency of managing Kubernetes namespaces and contexts by eliminating the need for remembering and entering detailed kubectl commands. With the infractl ns and infractl ctx commands, transitioning between different namespaces or contexts becomes seamless. This capability simplifies your operations and aids in effectively handling multiple environments. Additionally, Infractl’s built-in fuzzy search feature allows for quick viewing of available contexts and namespaces, making it easier to navigate through your Kubernetes infrastructure without constantly specifying namespaces or using the kubectl config use-context
Example Output:
Leveraging Infractl in CI/CD Pipelines
One of the key advantages about Infractl being a CLI tool is that it can be easily integrated into your CI/CD pipelines for post-cluster infrastructure testing. By incorporating Infractl into your automated workflows, you can perform essential checks and validations on your telco Kubernetes infrastructure, helping to catch potential issues before they impact your deployments. 🚀🚀
Here’s an example of how you can leverage Infractl in a Jenkins pipeline:
pipeline {
agent any
stages {
stage('Checkout') {
steps {
git 'https://github.com/johnlam90/infractl.git'
}
}
stage('Build') {
steps {
sh 'go build -o infractl'
}
}
stage('Test Infrastructure') {
steps {
sh './infractl multus -f tests/multus-config.yaml'
sh './infractl ssh <node-name> -c "systemctl status kubelet"'
sh './infractl get utilization'
sh './infractl sysctl'
}
}
stage('Deploy') {
steps {
// Deploy your telco application
}
}
}
}
Lightweight and Efficient
Despite its small size, Infractl packs a powerful punch when it comes to testing and debugging your infrastructure. It’s fast, reliable, and doesn’t add any unnecessary overhead to your systems. You can run Infractl on your local machine, in your CI/CD pipelines, or even on resource-constrained edge devices without worrying about performance impacts. 🌟
Written in Golang, it leverages the language’s inherent advantages—such as concurrency support and ease of deployment—to deliver a tool that’s both lightweight and blazingly fast.It can be cross compiled to run on various platforms and architectures.
Conclusion
Of course, Infractl is not perfect, and there’s always room for improvement. But I genuinely believe that it can make a meaningful difference in how we test our telco Kubernetes infrastructure. By simplifying the testing process and providing valuable insights, Infractl empowers us to build more robust and reliable clusters. 🚀
So, if you’re looking for a way to streamline your telco Kubernetes testing workflow, I recommend giving Infractl a try. It might just become your new best friend in the world of telco Kubernetes! 😄
Feel free to check out the Infractl GitHub repository at https://github.com/johnlam90/infractl to learn more and explore the source code. And if you have any questions or feedback, don’t hesitate to reach out to the community.
Happy testing, and may your telco Kubernetes clusters always be reliable and performant! 🙌
Cheers, John Lam